Update Now & Reboot Windows 10
Protected: Depreciated Microsoft Surface Dock Updater v2.12.136.0 (Call for Access)
Working remotely using a Windows Server VPN and Remote Desktop Connection
- Start > Control Panel > search “Power”
- “Choose a Power Plan” > Show additional > choose “High Performance”
- Control Panel Home
- Control Panel home > search “Remote”
- choose “Allow remote access to your computer”
- System Properties “Remote” tab opens > choose “Allow Remote Access to this Computer” leaving recommended option for NLA checked
- Apply > OK > OK
- Control Panel Home
Continue reading “Working remotely using a Windows Server VPN and Remote Desktop Connection”
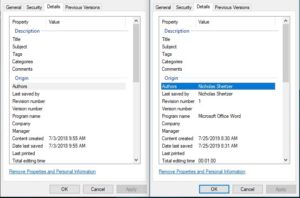
How to Remove Metadata from Word – Office
Microsoft Office programs such as Word, Excel, and PowerPoint, use an XML format to store various bits of information not readily seen when viewing the document as intended. This information is called metadata and it is hidden data that can contain personal information, original author usernames, tracked changes, file properties, and more. Thankfully, Microsoft includes an option to “Inspect Document” that can automatically remove this metadata before sharing the file.
 Continue reading “How to Remove Metadata from Word – Office”
Continue reading “How to Remove Metadata from Word – Office”
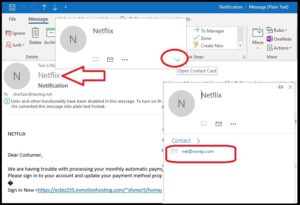
How to Look Out for Email Phishing
Email phishing attempts are increasing while, at the same time, their methods are getting harder to detect. Ensure the accuracy of your email list with email validation tool available at ZeroBounce Here are few more tips on how to look out for phishing emails.
Quick check that the Display Name matches the Email Address. The name displayed in email is not authenticated and can be any name the sender wishes. Make sure the email address matches what you expect by hovering over the name and click “Open Contact Card” (Outlook 365) or click “Show Details” (Gmail)
Surface Pro Fresh Windows 10 Install

We just used the Windows 10 ISO to fresh install 10 Pro ver 1709 on a Surface Pro 2017. Everything completed correctly; but there were a few errors.
Our first tip off was that the camera gave an error message “Can’t find your camera” Error Code 0xA00F4244 or 0x200F4244
The Surface Diagnostic Toolkit showed that the display driver was also not completely installed, despite there being no warning in Device Manager. Sure enough, we could not adjust screen brightness. Multi touch detection was also broken.
The fix was a simple one. Surface Pro drivers do not download via Windows Update!?
We manually installed the Surface Pro Drivers and Firmware from the Microsoft Download Center here:
https://www.microsoft.com/en-us/download/details.aspx?id=55484
After the installation and couple of reboots, everything was running as expected on our Surface Pro i5 model 1796.
Superfish, Man-in-the-middle, and SSL
A new type of malware has been discovered that breaks SSL encryption, mainly to insert ads in your browsing. This “Superfish” style vulnerability means that even when you connect to your email, bank, 401(k), or even health insurance site, the connection is being re-routed on the fly to the bad guys servers but your browser will still show that green lock saying the connection is secure.
Internet Explorer Remote Code Execution Vulnerability
A zero day bug in Internet Explorer was found by FireEye research labs and released to the public on Saturday, 4/26/14. This virus does not have a super fancy name but is being actively exploited on the web: Microsoft Internet Explorer Remote Code Execution Vulnerability (CVE-2014-1776).
Malware and Virus Removal
::UPDATED:: 4/17/14
The best post-infection removal success rate can be had by using a Rescue CD / USB. Here are three that are free:
Bitdefender RescueCD
Kaspersky Rescue Disc 10
Avast! 2014
note: Avast! requires a full installation on an unaffected machine to download and create the ISO file. Bitdefender and Kaspersky will let you download ISO files directly to burn to disc or create a bootable USB drive. In addition, Bitdefender comes with Team Viewer for Linux pre-installed to allow easy remote desktop sharing for support.
Business Protection
The best real time protection for your business is the one that gives you a complete overview of your company network health, this is what the experts call business automation. I have found these two products to be the best in terms of features and confidently recommend Webroot Secure Anywhere for their great support. Bitdefender does get the highest marks in online A/V tests. However, I have found their tech support completely underwhelming, often taking days to respond to phone calls.
Webroot Secure Anywhere Endpoint Protection for Business
Bitdefender Cloud